Digital access significantly influences cybersecurity by expanding the potential attack surface for cyber threats. Enhanced connectivity necessitates robust security measures to protect data.
How Does Digital Access Impact Cybersecurity? The digital era has ushered in unprecedented levels of connectivity. With the rise of internet usage, cybersecurity has become a fundamental pillar of digital operations. Easy access to digital resources allows for improved efficiency and innovation but also poses substantial risks.
Cybersecurity efforts must therefore evolve rapidly to address the challenges that come with increased digital access. Secure practices are vital to safeguard sensitive information from malicious actors. This balance of accessibility and protection is crucial for maintaining the integrity of our digital world. Every additional device connected to the internet is another potential entry point for cyber-attacks, making cybersecurity a dynamic and critical field in the face of expanding digital access.

Credit: papers.govtech.com
Which Statement Describes Cybersecurity
Cybersecurity encompasses measures to protect digital systems and data. As digital access grows, so does the potential for cyber threats, making robust security protocols vital for safeguarding sensitive information.
In today’s digital age, understanding cybersecurity is crucial to safeguarding our online presence. With the increasing reliance on digital solutions, the intersection of digital access and cybersecurity has never been more relevant. Let’s unpack the intricacies of cybersecurity and how it impacts every digital user out there.
What Is Cybersecurity?
Cybersecurity, at its core, involves practices, technologies, and processes designed to protect digital devices, programs, networks, and data from attack, damage, or unauthorized access. It’s akin to a digital fortress that safeguards information from the relentless onslaught of cyber threats lurking in the vast expanse of the internet.
Key Components Of Cybersecurity
Engaging in digital activities requires a robust cybersecurity strategy, and its key pillars include:
- Risk Management: Identifying and evaluating risks to mitigate their impact on information assets.
- Access Control: Ensuring that only authorized individuals have access to specific data or systems.
- Data Protection: Safeguarding important information from corruption, compromise, or loss.
- Incident Response: Having a planned approach to managing the aftermath of a security breach or cyberattack.
The Importance Of Cybersecurity In The Digital Realm
As digital access expands, the role of cybersecurity grows exponentially. Protecting sensitive data not only shields individuals from identity theft but also secures businesses against devastating cyberattacks that can lead to financial loss and reputational harm.
How Cybersecurity Is Implemented
To truly grasp the effectiveness of cybersecurity, one must look at its practical application:
- Encryption: Transforming data into a secure format during transmission, only accessible via a decryption key.
- Firewalls: Serving as a barrier between secure internal networks and untrusted external networks, such as the internet.
- Antivirus Software: Detecting, preventing, and removing malware from computers and networks.
- Security Protocols: Guidelines and standards used to secure communication over the internet.
In leveraging these tools, individuals and businesses alike can navigate the digital landscape with confidence, knowing they are protected by the vigilant eyes of cybersecurity measures. Whether entering the realm of e-commerce, sharing sensitive communications, or simply browsing for information, cybersecurity is the unsung hero shielding our digital endeavors from invisible threats.
What Is The Goal Of An Explorer In Cyber Security
Explorers in cybersecurity aim to unearth vulnerabilities and safeguard digital environments. Their goal aligns with the broader theme that digital access amplifies the need for robust cybersecurity measures.
As our digital lives become more integrated with daily activities, understanding the repercussion of that connectivity is paramount. Digital access not only enables individuals and organizations to interact with a complex web of devices and databases but also presents significant challenges for cybersecurity.
Allowing multiple entry points for access also creates multiple vulnerabilities.
What Is Cybersecurity Exploration?
In the field of cybersecurity, exploration refers to the proactive search for knowledge about potential security threats and vulnerabilities within a system. Explorers, often known as ethical hackers or penetration testers, embark on a journey to:
- Identify weak spots: Detecting points in the system where a breach is more likely to occur.
- Gather intelligence: Collecting information about current security trends, hacking techniques, and the latest malware.
- Test defenses: Attempting to breach the system in a controlled environment to test the robustness of security measures.
- Innovate protection methods: Developing new ways to protect systems against the ever-evolving threats.
This constant vigilance helps organizations stay one step ahead of malicious hackers, safeguarding their digital assets and maintaining user trust.
Goals Of A Cyber Security Explorer
The primary aim for a cybersecurity explorer is to ensure that systems and data remain impregnable against unauthorized access. The hierarchy of objectives includes:
- Preventing data breaches: Safeguarding sensitive information to maintain confidentiality and integrity.
- Ensuring compliance: Meeting regulatory standards that govern data security to avoid legal repercussions and fines.
- Educating stakeholders: Sharing knowledge with employees, customers, and partners to strengthen an organization’s overall security posture.
- Facilitating safe digital access: Allowing users to engage with digital assets securely, without compromising on functionality or ease of use.
As businesses and individuals become increasingly reliant on digital services, the importance of cybersecurity exploration cannot be overstated. It is a dynamic and continuous process that adapts to new threats and shapes the future of digital safety.
A Protects Your Device Against Unauthorized Access
Digital access directly shapes cybersecurity by deploying robust authentication methods to shield devices from illicit entry. Implementing strong access controls is vital for safeguarding sensitive information against digital intrusions.
The Vitality Of Digital Access In Cybersecurity
In the ever-evolving digital world, our personal and professional lives hinge significantly on the strength of cybersecurity measures. Digital access not only opens doors to vast information but also exposes us to potential cyber threats. Hence, a robust shield to safeguard against unauthorized access is no longer optional but a necessity.
Here’s how enhanced digital access directly influences the security of our virtual environments.
Strong Authentication Mechanisms: Key To Robust Defense
A robust authentication process is the first line of defense in cybersecurity. With digital access requiring varying levels of authorization, the importance of secure authentication cannot be overstated:
- Multi-factor Authentication (MFA): This adds layers to the security by requiring multiple forms of verification. It’s critical to prevent unauthorized access because even if one credential becomes compromised, an additional barrier still protects the device.
- Regular Update of Passwords: Implementing a policy for changing passwords regularly minimizes the risk of breaches. It ensures that compromised data doesn’t stay useful for long, thereby deterring continuous unauthorized access.
- Use of Biometrics: Incorporeting biometric verification, like fingerprint or facial recognition, offers a unique and difficult-to-replicate method of securing devices against unwarranted entry. Each user’s physical attributes provide a powerful tool for personalized security.
Impact Of Access Management On Cybersecurity Practices
When it comes to access management, controlling who gets into what corners of our digital space is key to maintaining a secure online presence. Let’s delve into how proper access control fortifies cybersecurity:
Access management involves defining user roles and granting permissions based on these roles. By delineating clear access boundaries, one can protect sensitive data while ensuring necessary information is available to the right people. Setting strict limitations on who can view, modify, or distribute information creates a secure architecture that is considerably more resistant to cyber attacks.
The Role Of Continuous Monitoring And Alerts
Continuous monitoring and prompt alerts function as crucial components in the cybersecurity equation. Their role cannot be emphasized enough:
- Real-time Monitoring: By keeping track of access and activities within the system, one can quickly identify and respond to any unusual behavior, effectively reducing the reaction time in the face of a breach.
- Automated Alerts: These serve as early warning systems, notifying administrators and users of potential security events. Prompt detection through alerts means quicker resolution, which could be the difference between a minor incident and a major breach.
By incorporating these strategies, the impact of digital access on cybersecurity becomes profoundly positive, reinforcing the barriers that protect our precious data and privacy in the digital realm.
Which Cyber Protection Condition
Digital access widens the cybersecurity battlefield, necessitating robust protection strategies to guard against increased vulnerabilities. Enhanced digital connectivity exposes users to more cyber threats, making resilient cyber protection conditions essential for safeguarding data integrity.
In today’s digital age, where the internet is ubiquitous, understanding the ways in which digital access influences cybersecurity is critical. The ease of connectivity also opens doors for cyber threats, making the need for robust cyber protection mechanisms imperative.
The Necessity Of Strong Authentication Protocols
With the rise of digital platforms, enforcing strong authentication protocols is imperative for securing user data. These protocols act as the first line of defense against unauthorized access, safeguarding both personal and corporate information from potential breaches.
- Multifactor authentication (MFA): MFA adds an extra layer of security by requiring additional verification methods beyond just passwords, such as one-time codes or biometric scans.
- Password policies: The enforcement of complex password requirements helps prevent brute force attacks by making passwords harder to guess or crack.
Impact Of Software Updates On Security
Keeping software up-to-date plays a crucial role in fortifying cybersecurity. Software updates often include patches for security vulnerabilities that have been discovered since the last iteration of the software was released.
- Patch management: Regularly applying patches closes security holes and protects against exploitation by hackers who exploit outdated software.
- Update reminders: Prompt users with reminders to update their software can reduce the window of opportunity for cyber attacks to take advantage of outdated systems.
Education And Awareness As A Cyber Defense Mechanism
Ignorance is a cybercriminal’s best friend. Educating users about cybersecurity risks and best practices can significantly reduce the chances of a security breach.
- Phishing awareness: Training individuals to recognize phishing attempts ensures they are less likely to fall victim to such scams and compromise sensitive information.
- Safe browsing habits: Instilling habits such as avoiding suspicious links and downloads helps prevent malware infections and data theft.
The Role Of Data Encryption In Privacy Protection
Data encryption is a vital component in the crusade to protect sensitive information from prying eyes. Encrypted data ensures that even if intercepted, the information remains unreadable and secure.
- End-to-end encryption: This technique secures data as it travels from sender to receiver, thwarting efforts by cybercriminals to intercept and decipher messages.
- Encryption at rest: Protecting stored data on devices and servers prevents unauthorized access to information, even in the event of a physical breach.
In the maze of the digital ecosystem, the interplay between digital access and cybersecurity is complex and ever-evolving. As cyber threats morph and proliferate, staying ahead with stringent cyber protection conditions becomes not just a recommendation, but a compulsion for individuals and organizations alike.
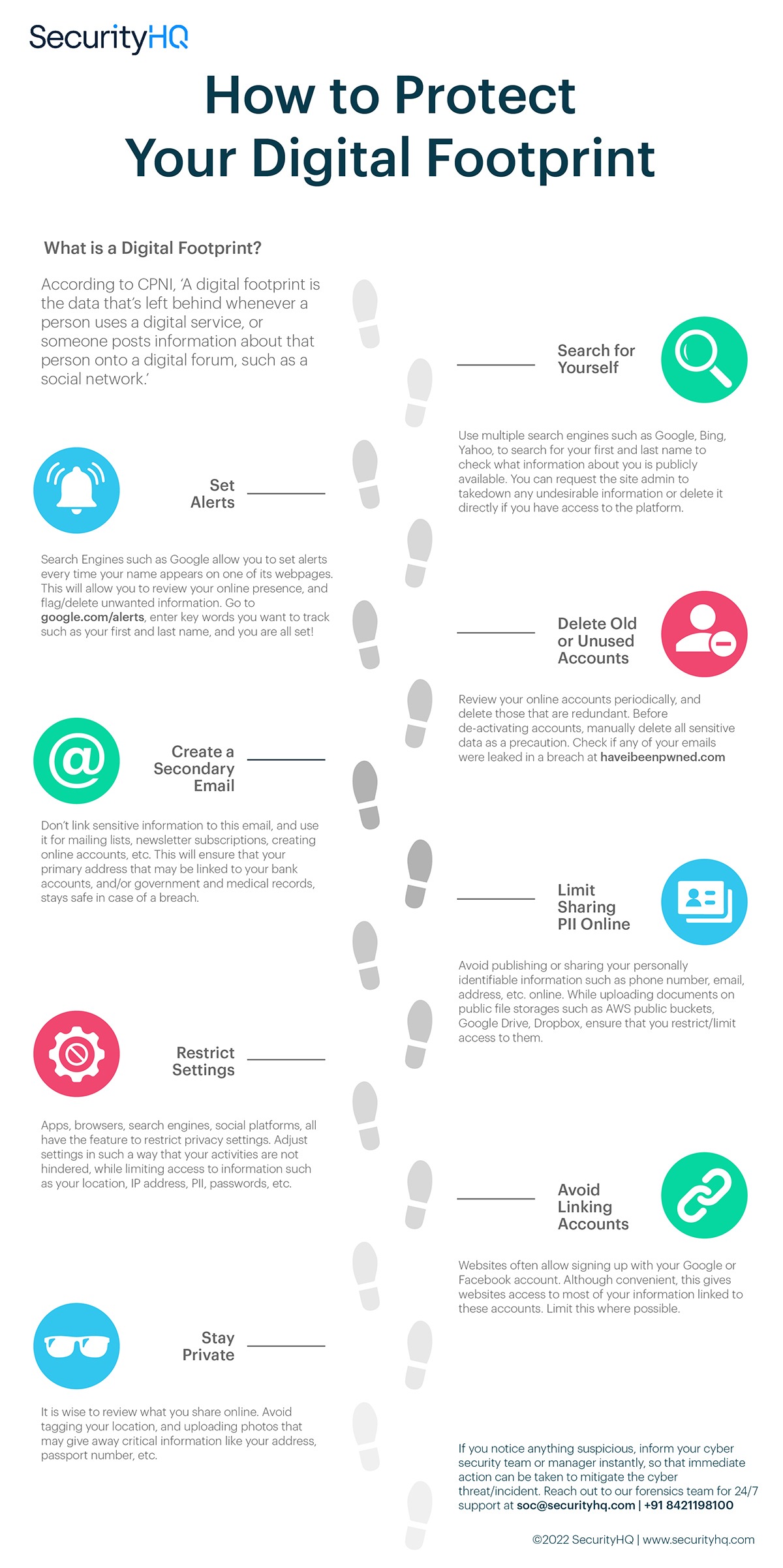
Credit: www.securityhq.com
Frequently Asked Questions On How Does Digital Access Impact Cybersecurity
What Is The Impact Of Digitization On Cybersecurity?
Digitization increases data volume online, creating more targets for cyber attacks. This demands stronger cybersecurity measures to protect sensitive information and maintain user trust.
How Is Digital Access Impacts Various Areas Of Cybersecurity?
Digital access expansion increases cybersecurity challenges by potentially exposing more entry points for attacks and necessitating advanced defense measures across networks and devices to protect sensitive data.
How Does Digital Divide Impact Cybersecurity?
The digital divide exacerbates cybersecurity risks by limiting access to cyber education and resources for vulnerable populations, making them more prone to cyber attacks.
How Does Technology Affect Cyber Security?
Technology advancements enhance cybersecurity by offering robust protection tools. Conversely, new tech creates fresh vulnerabilities and sophisticated cyber threats, demanding continuous security updates and vigilant monitoring.
Conclusion
As we embrace digital expansion, the stakes for cybersecurity rise exponentially. Secure access is now non-negotiable; it’s the bulwark against cyber threats. By prioritizing robust defenses and ongoing education, we safeguard our digital frontiers. Let’s commit to cyber resilience, ensuring safe and secure digital access for everyone.
Stay vigilant, stay protected.

